About the Course
The entire course enables attendees to progress from having no skills to an advanced level of reverse engineering. The level attained depends on both the duration of the course and the effort put in. The entry-level course spans a total of 3 days, during which low-level computing and the basics of architectures are explained. Additional days contribute to leveling up to intermediate and advanced levels, where knowledge is solidified and tools are introduced to speed up the reverse engineering process, making it shorter and more reliable.
The primary target architectures of this course are Intel x86 and AMD x64, where we cover the fundamentals of computing and assembly language. Throughout the course, we will explore how to create basic programs in both C and assembly, and then explore the process of reverse engineering using disassemblers, decompilers, and debuggers on various operating systems, including Windows and Linux.
Each day of the course emphasises hands-on labs, allowing participants to apply their newly acquired knowledge in practical exercises. Theory alone quickly fades, so our main objective is to help you acquire useful, long-term knowledge by putting it into practice.
Every challenge builds upon the previous one to ensure continuous learning and the overcoming of new obstacles. This approach allows knowledge to be built up reliably and quickly, without wasting time, which is one of the main objectives of this training. The labs are fun and entertaining, providing a great reward for those who can solve them.
The training employs state-of-the-art tools and techniques that mirror those utilised in real-world situations. Any knowledge acquired during the training can be readily applied to real-life objectives following the course.
High-level overview
- Introduction to the environment and tools
- Introduction to the x86 and x64 architectures
- CPU basics including registers, ALU, CU, memory and I/O
- Relation of assembly programming and machine code
- Opcodes, operands, machine code and their disassembly
- Stack, heap, calling conventions, pointers, and data structures
- Debugger usage on Windows and Linux (gdb, x64dbg, windbg)
- Disassemblers, decompilers, and symbols (IDA Free, Ghidra)
- Game Hacking: modifying program behaviour to cheat
- Shared Objects and Dynamic Link Libraries
- Windows API and System calls
- Tools to enhance the effectiveness of reverse engineering (FunctionID, FindCrypt, Ret-Sync, etc.)
- Unicorn Engine to run native code
- Basics of Malware Reverse Engineering
- Finding and fixing security vulnerabilities: Stack based buffer overflows, weak random number generation etc.
- Code deobfuscation
A detailed agenda is provided below.
Take a peek, try yourself
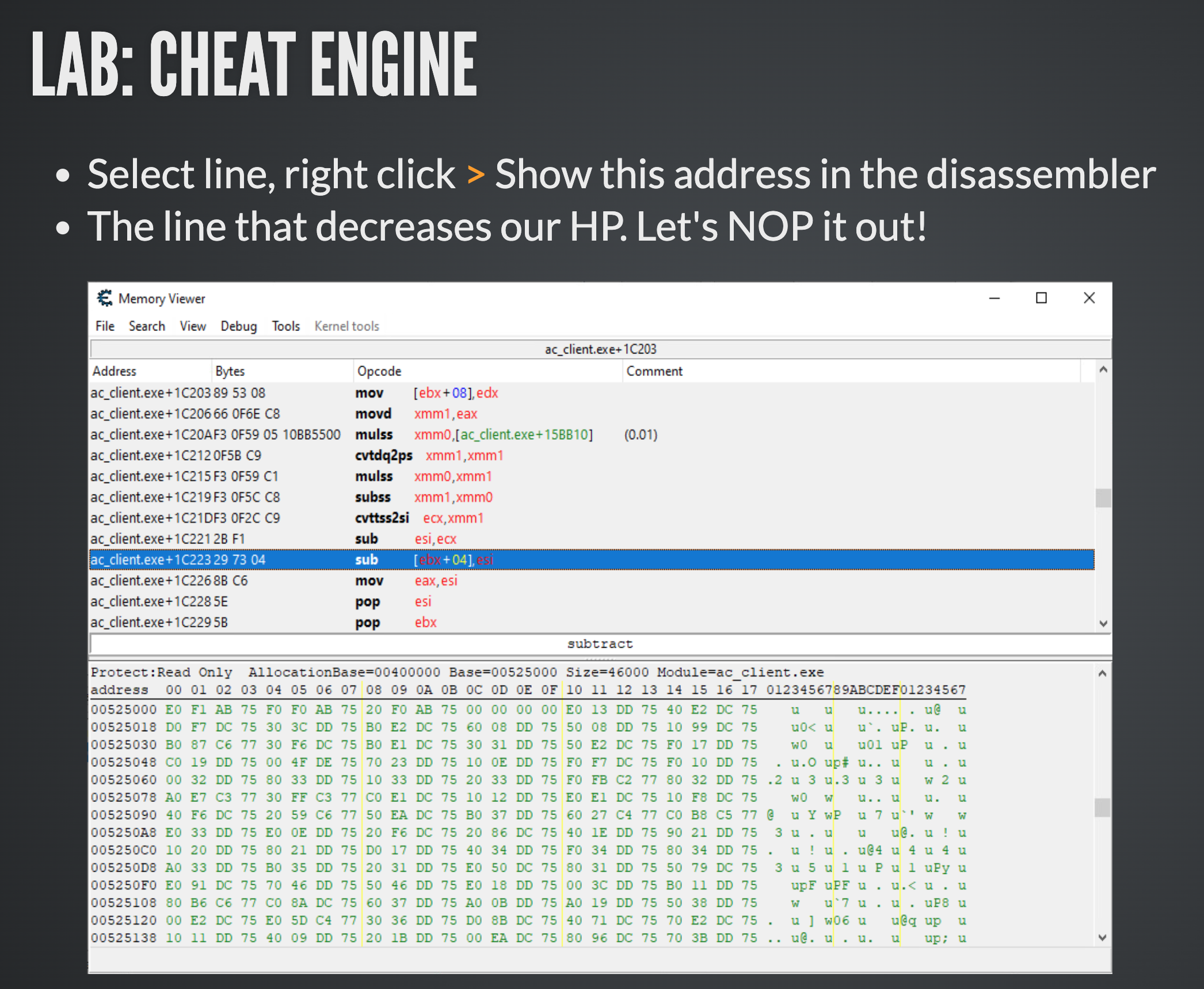
Game Hacking
Have you ever wondered how cheats are created?
Cheat Engine is a powerful tool that can assist reverse engineers in identifying memory addresses storing crucial data for the program being executed. Utilising it with games enhances the enjoyment of reversing by providing quick rewards. Discovering memory addresses for values such as health, experience points, or ammo could render the player immortal and invincible.
Throughout the course, we explore the application of Cheat Engine and patch games to introduce additional fun to assembly and reverse engineering. By patching instructions in the program code, permanent cheats can be created within the game. This effectively showcases the power of understanding assembly code.
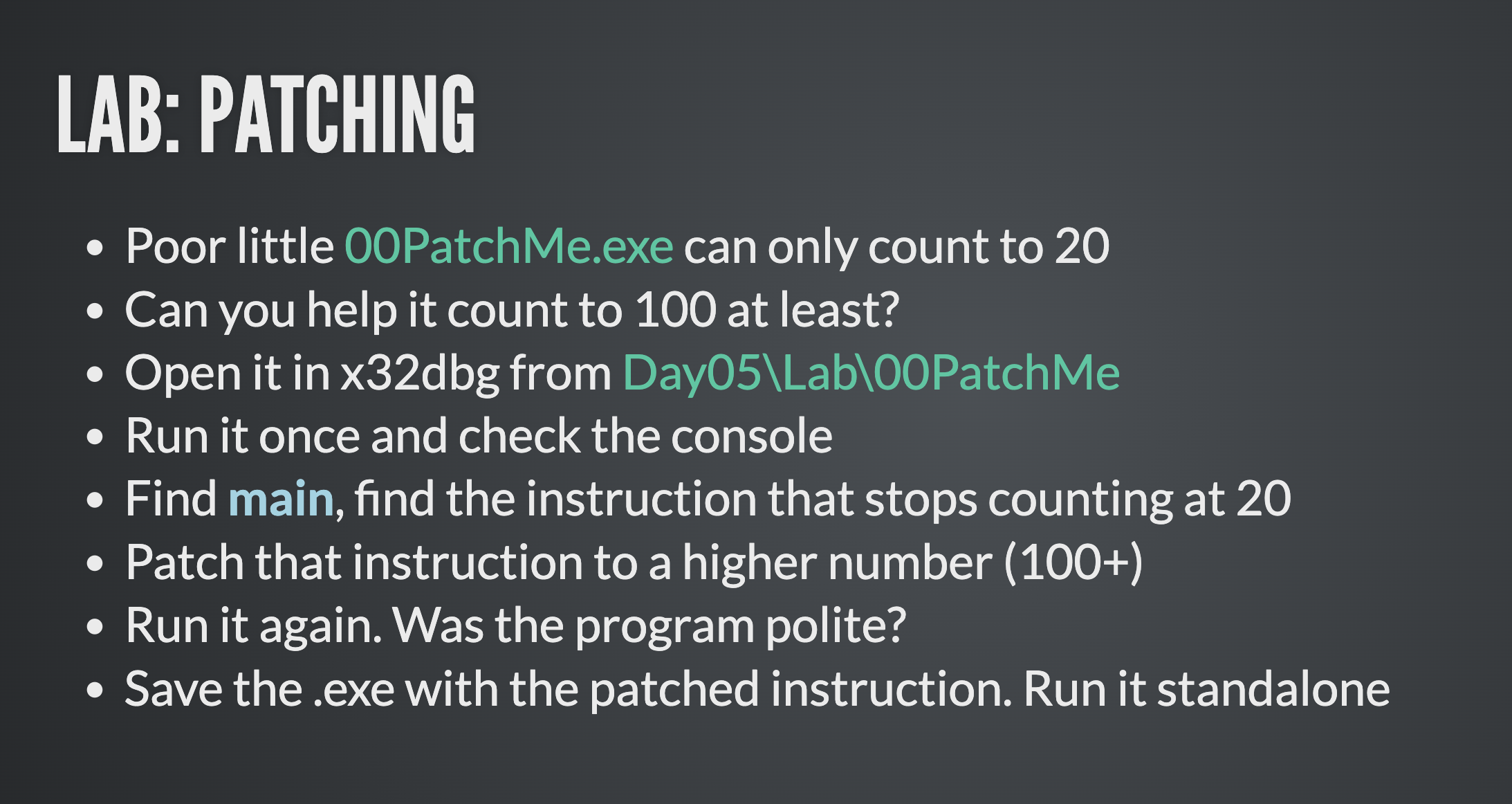
Challenge Yourself!
Still unsure about the course?
Download the following two files and put your skills to the test:
- 00PatchMe-source.zip
- 00PatchMe-binary.zip - password: IWantIn!
Can you assist the program in counting above a hundred?
Compile the binary yourself if you prefer not to run untrusted binaries downloaded from the Internet!
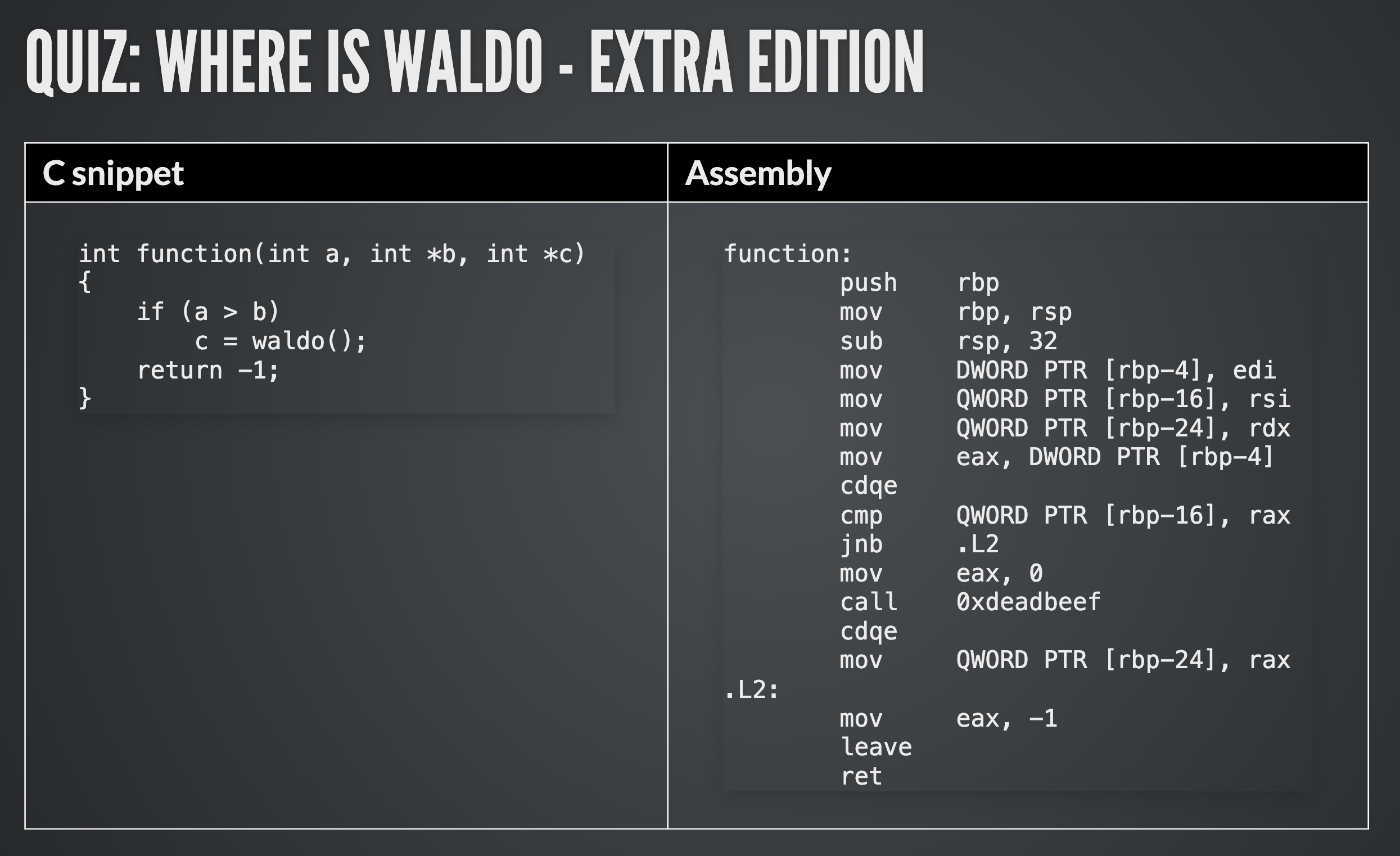
Where is Waldo?
One of the quiz questions in the course that involves analysing the simple C code on the left, which was compiled into machine code and then disassembled.
Can you find Waldo in the assembly code? What's his address?
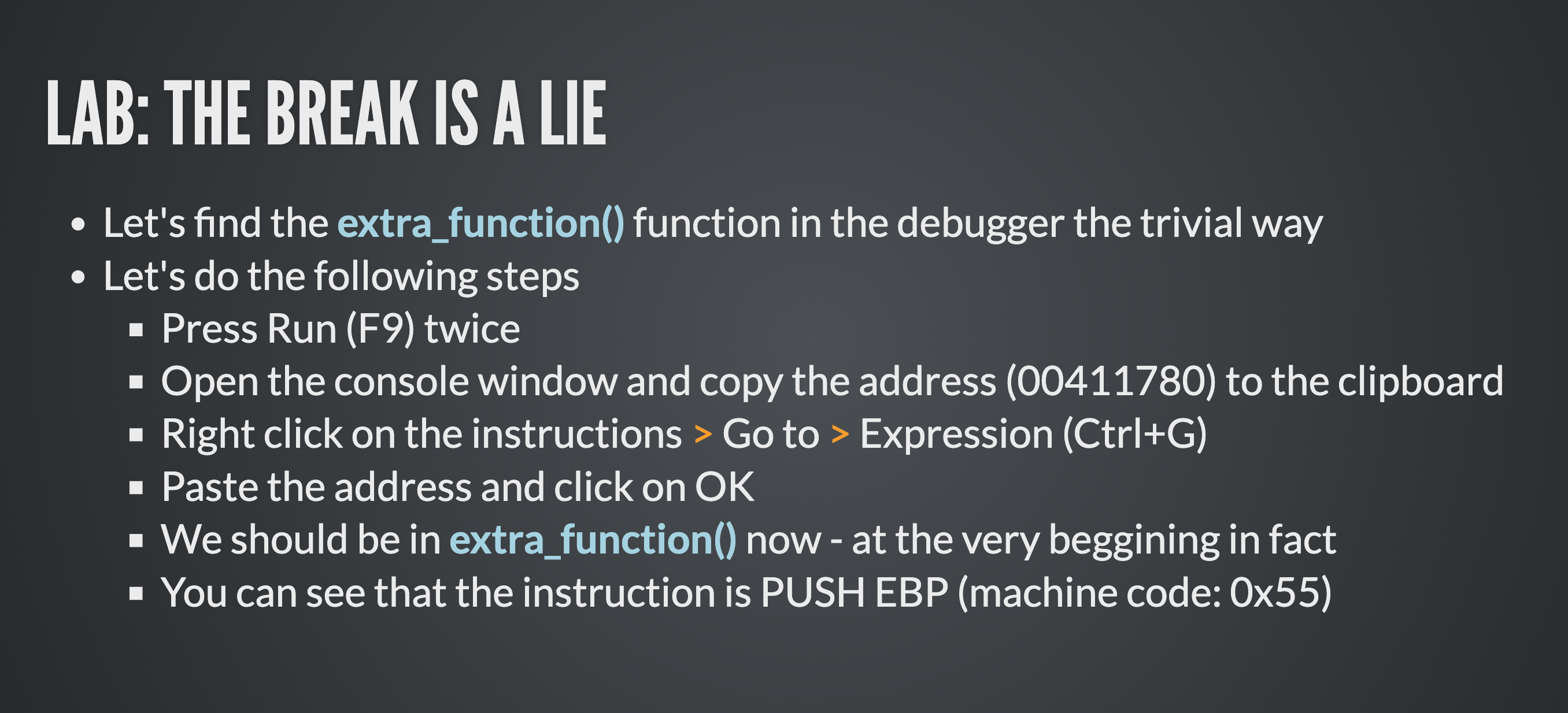
Break Is A Lie
Going deeper and deeper into the course, we can realise that not everything we see is real. Even the debuggers lie to us!
Software breakpoints set might show different values in memory than in the debugger. How is this possible and why is it done this way?
The cake break is a lie.
Detailed Agenda
The duration of the course varies depending on the desired level of proficiency. The 3-day course provides a solid foundation for absolute beginners who possess programming knowledge, but lack experience in software reverse engineering.
An additional two days (totaling 5 days) further solidifies this foundation by diving into operating systems and their relation with assembly language.
Completing the full 10-day course elevates attendees to an advanced level, where they gain proficiency in using tools and techniques to expedite processes.
Days 1 to 3 (Beginner Level):
- Environment delivery and setup
- Introduction to the Windows and Linux environments and tools
- Basics of computing: CPU, ALU, CU, Memory and I/O
- Definitions of assembler, disassembler, compiler and decompiler
- Data or code
- Data representation and endianness
- Assembly, machine code, opcodes and operands
- Common instructions and assembly syntax
- Registers and flags on x86 and x64, data sizes
- Unconditional and conditional jumps and their relation to flags
- Data movement and addressing modes
- Arithmetic and logic operations
- Differences between architectures
- Debuggers on Windows and Linux
- Basic and advanced operations in debuggers (stepping, tracing, altering control-flow, patching)
- Software and hardware breakpoints
- Understanding the relationship between C and Assembly via code
- Recovering basic data structures (types, return values, arrays, structs, pointers)
- Recovering basic programming logic (if statements, loops, switches)
- Portable Executable (PE) file format
- Process memory map (sections, stack, heap, DLLs)
- Heap vs. Stack: layout and location
- Stack-related operations, stack frames, epilog and prolog (x86 and x64)
- Base pointer usage
- Calling conventions on Windows and Linux (x86 and x64)
Days 4 to 5 (Intermediate level):
- Symbols on Windows and Linux
- Shared Objects and Dynamic Link Libraries
- Exports and Imports
- Windows API Basics
- Utilising Windows API in C and Assembly
- Function decoration/Name mangling
- Transitioning between User mode and Kernel mode
- Interrupts and system calls
- System calls on Windows and Linux
- Debugger theory
- Different methods of debugging a program (Execute, Attach, Postmortem)
- Advanced debugger usage (x32dbg, x64dbg, and WinDbg)
- Utilisation of Ghidra and IDA Free (disassembly, decompiling, auto-analysis, ...)
- Working without symbols
- Locating main() functions
Days 6 to 10 (Advanced level):
- Debugging on Linux (GDB, GDB-Server)
- GDB Enhancements
- Executable and Linkable Format (ELF) explained
- Static and Dynamic Linking
- Early and Lazy Binding
- Sections in a Unix process
- Position-Independent Executable (PIE) and Address Space Layout Randomization (ASLR)
- Debugging Threads in GDB
- Recreating Structs in Ghidra
- Data Types in Ghidra
- Tools to enhance the effectiveness of reverse engineering:
- XAnalyzer
- FunctionID
- FindCrypt
- Ret-Sync
- BinDiff/BinExport
- Unicorn Engine in depth to run native code
- Creating disassemblers with Capstone
- Recovering Cryptographic algorithms with the Unicorn Engine
- Basics of Malware Reverse Engineering:
- Static and Dynamic analysis of the executable
- Reverse engineering part of the malware codebase
- Finding and fixing security vulnerabilities:
- Stack-based buffer overflows
- Format string vulnerabilities
- Integer over- and underflow
- Command Injection
- Weak random number generation
- Code deobfuscation
- Cryptographic challenges
Prerequisites
Proficiency in coding
A solid understanding of any programming language is important, but what truly matters is a strong grasp of programming logic, regardless of the language used.
Competence in Windows and Linux
Competence in utilising both operating systems with confidence.
Computer that is capable to virtualize x64 architecture.
Please note that ARM-based notebooks, including newer MacBooks, are not compatible with the training.

Deliverables
Training material
The slide deck utilised for the presentation contains all the technical information covered throughout the course, serving as a comprehensive reference resource.
Virtual machines
In the case of offline delivery, attendees are provided with Windows and Linux machines, which they are allowed to keep even after the training concludes.
Labs and challenges
All labs and challenges are provided for practice during and after the training, ensuring continuous learning and skill development.
Reverse Engineering knowledge
The training provides attendees with foundational low-level computer knowledge and reverse engineering skills, empowering them with expertise that remains invaluable.
Contact
Contact Us

